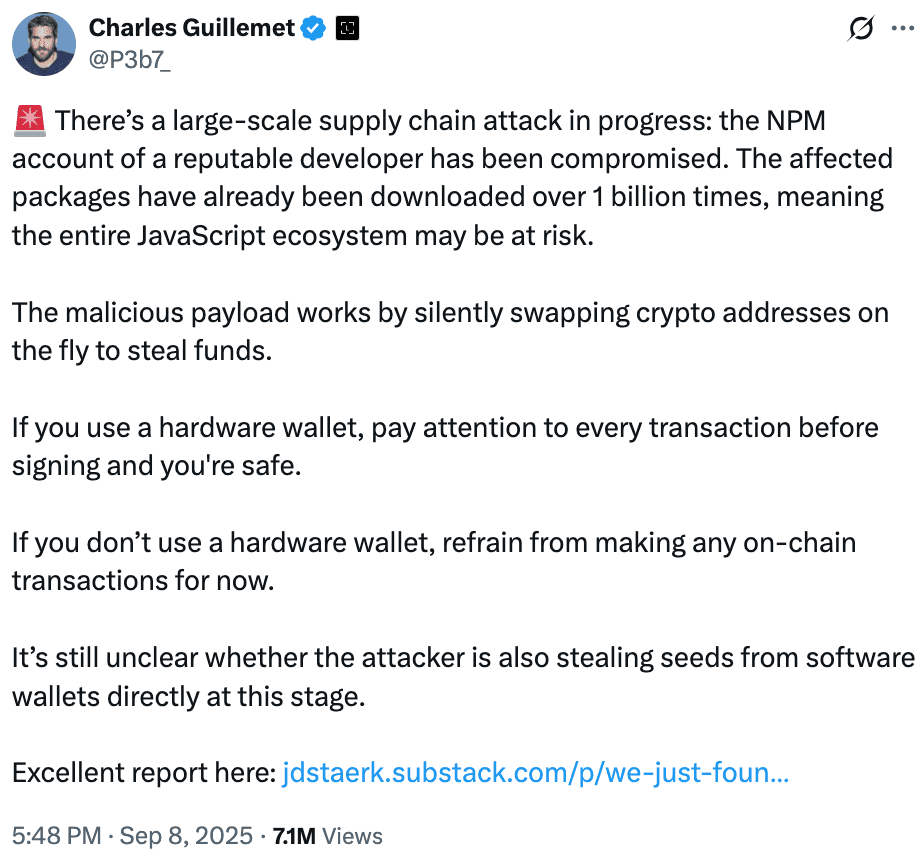
On September 8, a significant software supply chain attack was discovered within the NPM ecosystem, affecting several widely used JavaScript libraries. The incident first came to public attention when Charles Guillemet, Chief Technology Officer of Ledger, issued a warning that the Node Package Manager account of a trusted developer had been compromised. Early assessments suggested that more than one billion downloads were exposed to hidden malware designed to steal cryptocurrency. Subsequent investigations, however, revealed that the compromised packages collectively represent more than 2.6 billion weekly downloads.

Supply Chain Attack Exposes Over 2 Billion
Supply Chain Attack Exposes Over 2 Billion
The attack focused on the account of a developer known as “qix,” who maintains several popular JavaScript libraries. These include chalk, strip-ansi, color-convert, and debug, all of which are used across countless projects in both server-side and front-end environments. The attackers gained access to the account through a fake support email and pushed malicious updates to around 18 packages. Because of automated dependency installs, the malware spread rapidly within hours of the breach.
Guillemet explained that the malicious code was designed to silently replace cryptocurrency wallet addresses during transactions. This exposed users who rely on software wallets to the risk of losing funds if they approved transactions without noticing that the recipient address had been altered.
Malware Crypto Clipper and MetaMask
Security researchers identified the malware as a type of “crypto clipper.” It functions by replacing wallet addresses at different stages of a transaction. In cases where no wallet is detected, the malware modifies outgoing data within decentralized applications by hooking into browser functions such as fetch and XMLHttpRequest. This allows it to scan and alter addresses within application data.
If a wallet extension such as MetaMask is detected, the malware becomes more direct by intercepting the transaction before it is signed. It modifies the wallet address in memory so that when the user reviews the transaction, the fraudulent address is already in place. The malware relies on the Levenshtein algorithm, which generates addresses that closely resemble the original. This similarity makes it less likely that users will identify the alteration.
Supply Chain Attack Exposes Over 2 Billion
First Signs of the Attack
Developers first encountered signs of the attack when build systems returned an unexpected error message. Further inspection of a dependency called error-ex revealed obfuscated code that contained a suspicious function named checkethereumw, which indicated targeting of Ethereum wallets. Analysts later confirmed that the malware contained references to wallet addresses across several blockchains, including Bitcoin, Ethereum, Solana, Tron, Litecoin, and Bitcoin Cash.
Among the affected packages were some of the most widely used in the JavaScript ecosystem. Chalk alone receives more than 300 million weekly downloads, debug more than 350 million, and strip-ansi more than 260 million. In total, the compromised libraries are collectively downloaded more than 2.6 billion times each week, highlighting the depth of the impact across the developer community.
Hardware vs Software Wallets
Although many of the infected libraries are not directly linked to cryptocurrency projects, their integration into dependency chains means that even unrelated applications may have been exposed. Projects that interact with cryptocurrency wallets and decentralized applications are considered to be at the highest level of risk.
According to Guillemet, users of hardware wallets with clear-signing features remain safe because such devices allow them to verify every transaction before approval. By contrast, users of software wallets face greater exposure and are advised to exercise extreme caution until dependencies have been fully reviewed and secured.
Finding the Attacker and Funds Stolen
The attacker’s cryptocurrency addresses have been identified and are being actively monitored thanks to the transparency of public blockchains. A primary Ethereum address linked to the operation is 0xFc4a4858bafef54D1b1d7697bfb5c52F4c166976, along with several other backup addresses. At the time of reporting, the stolen funds had not been moved. This monitoring provides an opportunity for ongoing analysis, though the full scope of stolen assets remains unclear.
Supply Chain Attack Exposes Over 2 Billion
JavaScript and Community Role
The JavaScript and web3 communities have acted quickly to contain the incident. Malicious versions of the compromised packages have largely been removed from the registry, but risks remain for projects that may still rely on outdated versions within their lockfiles. Developers are being urged to audit their dependencies, lock safe versions, and reinstall clean builds to prevent further exposure.
Security professionals also recommend that developers rotate credentials, enforce two-factor authentication on accounts such as NPM and GitHub, and use deterministic installation methods like npm ci to maintain strict version control. Additionally, users are advised to carefully verify all cryptocurrency transactions, particularly if relying on software wallets.
Final Thoughts
This incident has been described as one of the most extensive breaches to affect the NPM ecosystem. While the community response was relatively swift, the attack underscores the fragility of modern software supply chains and the risks created by widespread reliance on open-source components.
As Guillemet emphasized, reviewing every transaction before signing remains essential. The breach serves as a reminder that even small libraries embedded deep within application infrastructure can become significant attack vectors when compromised. For developers and users alike, ongoing vigilance is now a critical part of maintaining security in the web3 and software development ecosystems.



