Seedify, a web3 incubator known for supporting gaming and metaverse projects, confirmed that its SFUND token bridge was exploited on September 23. Attackers managed to steal more than $1.2 million by minting unauthorized tokens and moving them across multiple chains. The hack, which shook community trust, has been linked to a North Korean state-affiliated group with a history of targeting web3 infrastructure.
Seedify Suffers $1.2 Million Breach
How Attackers Gained Access
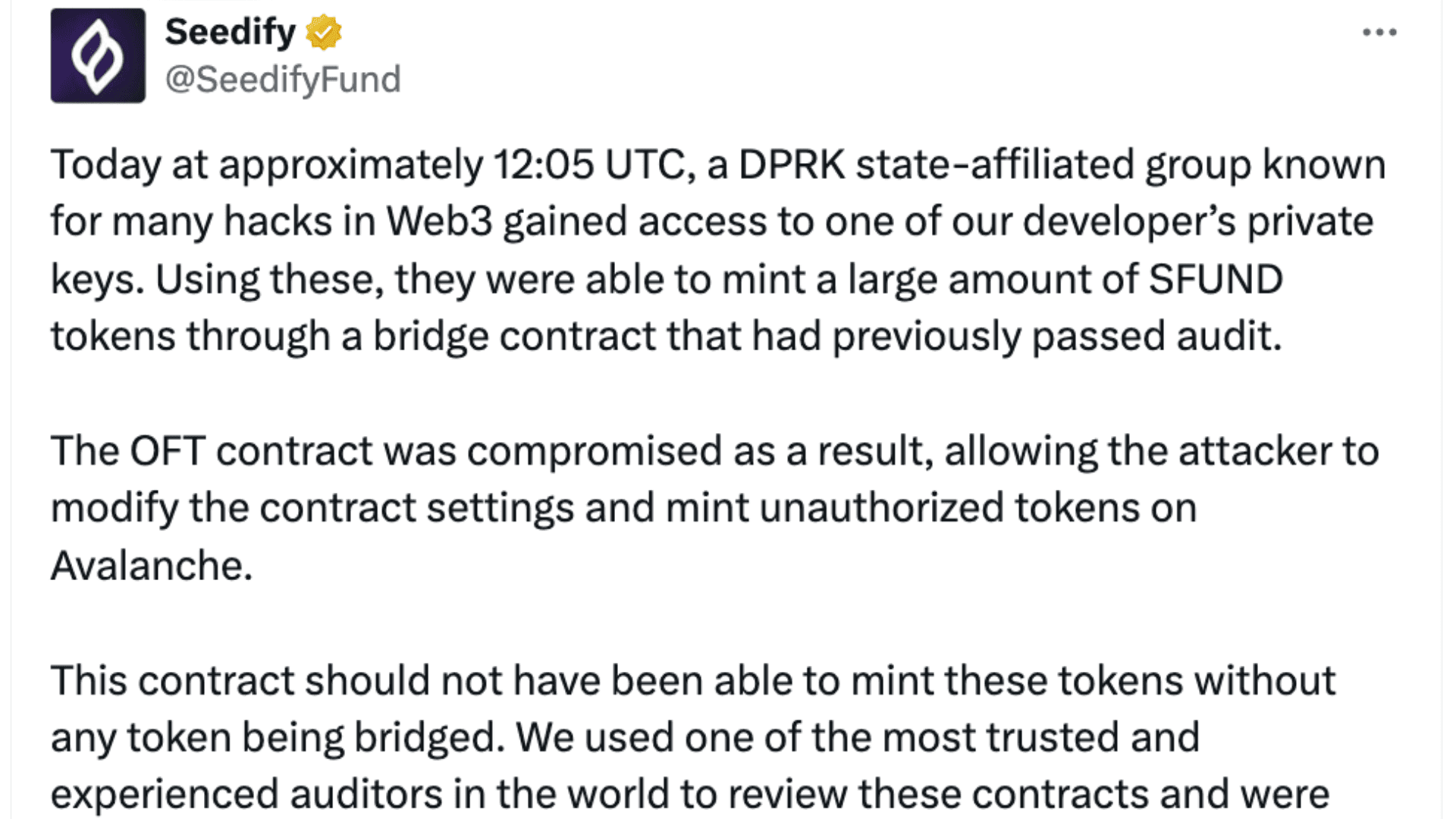
According to Seedify, the breach occurred when a stolen developer key was used to take control of its OFT bridge contract. Although the contract had previously passed security audits, the attackers were able to bypass normal checks by exploiting the permissions tied to the compromised key. This allowed them to mint a large amount of new SFUND tokens on Avalanche without actually moving funds between chains.
The tokens were quickly bridged to Ethereum, Arbitrum, and Base, where liquidity pools were drained. The final and most damaging stage unfolded on BNB Chain, where the tokens were rapidly sold before controls could be enforced.
The fallout was immediate. SFUND’s price fell by nearly 60 percent in less than a day, briefly dropping to $0.0537 before recovering closer to $0.25. Around 64,000 token holders on BNB Chain were directly affected, as their holdings either lost value or were diluted by the sudden influx of tokens. While some of the stolen funds, estimated at $200,000, were frozen by HTX, the majority remain unrecovered.
Seedify Suffers $1.2 Million Breach
Emergency Response from the Team
Seedify moved quickly once the exploit was identified. Bridge operations were suspended, token activity across affected chains was paused, and compromised permissions were revoked. Attacker wallets were blacklisted, and trading on centralized exchanges was temporarily halted to reduce market volatility.
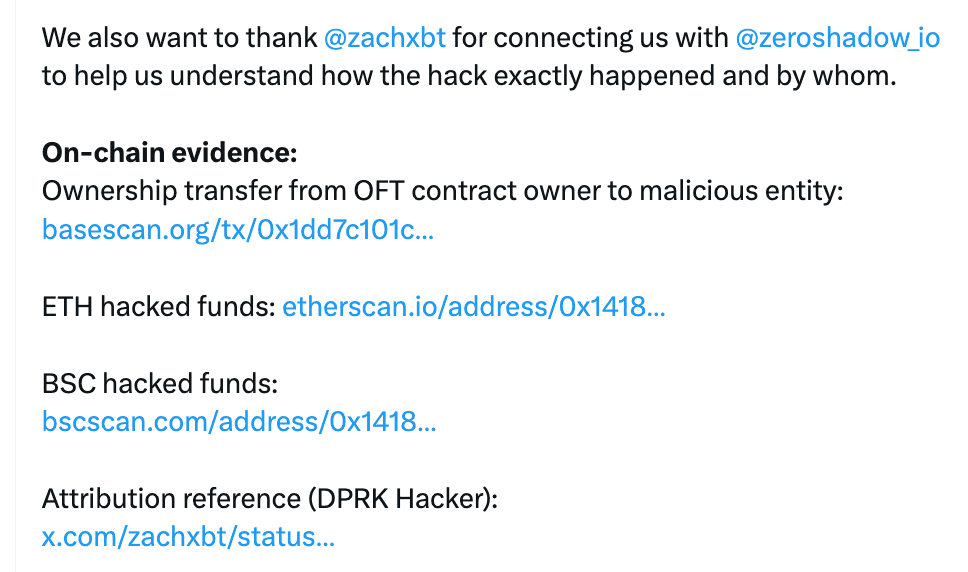
The team emphasized that the exploit only affected a single compromised wallet. User wallets, core contracts, and the broader Seedify protocol were not directly impacted. Security audits are now being revisited, with outside partners brought in to review the platform’s infrastructure.
Investigations led by blockchain analysts, including ZachXBT and ZeroShadow, linked the attack to a North Korean state-backed group. The same group has been tied to several other high-profile web3 exploits, and the speed of the Seedify operation matched tactics used in prior incidents.
Seedify Suffers $1.2 Million Breach
The Phoenix Raise Recovery Effort
In response to the attack, Seedify’s founder Meta Alchemist announced a recovery initiative called the Phoenix Raise. This plan is designed to compensate users who lost funds, strengthen the platform’s security systems, and stabilize the SFUND economy through buybacks. The team also confirmed that a full migration of the SFUND token is being prepared, though no timeline has been shared.
Seedify said the Phoenix Raise will also fund growth and marketing efforts as the platform transitions toward a permissionless launchpad model. Until migration details are finalized, users have been advised to only interact with SFUND on BNB Chain.

Seedify Suffers $1.2 Million Breach
The Bigger Picture for Web3 Security
The Seedify exploit is a reminder of the vulnerabilities facing web3 platforms, particularly cross-chain bridges. Even contracts that pass audits remain exposed if private keys are compromised. The incident has renewed calls for projects to adopt stricter safeguards, such as multi-signature approvals and time-delayed transactions for critical operations.
The Seedify exploit was not the only security issue to make headlines this week. A Twitch streamer known as RastalandTV lost more than $32,000 in crypto live on stream after downloading a malware-infected game on Steam. The stolen funds were donations raised for his cancer treatment, sparking outrage and leading to community-driven fundraising efforts. The malware has since been tied to more than 260 cases and over $150,000 in total losses.
Frequently Asked Questions (FAQ)
What happened to Seedify?
Seedify’s SFUND bridge was exploited on September 23 after attackers gained access to a developer key. Unauthorized tokens were minted and sold across multiple chains, resulting in more than $1.2 million in losses.
Who hacked Seedify?
Seedify attributed the exploit to a North Korean state-linked hacking group known for previous web3 attacks. Blockchain analysts, including ZachXBT and ZeroShadow, supported this conclusion.
What is the Phoenix Raise?
The Phoenix Raise is Seedify’s recovery plan aimed at compensating users affected by the exploit, improving security, stabilizing SFUND through buybacks, and funding the platform’s future growth.
Is SFUND still safe to use?
Seedify has advised users to only use SFUND on BNB Chain until a token migration is complete. Core contracts and user wallets were not directly compromised in the attack.
Will Seedify recover lost funds?
Around $200,000 of the stolen assets were frozen by HTX, but most of the funds remain unrecovered. The Phoenix Raise initiative is intended to cover user losses and strengthen the ecosystem going forward.



